
Congratulations to our winners and thank you to all who submitted a video for this year's contest! You are all THE SHIELD!
SCROLL DOWN TO VIEW THE WINNING VIDEOS!
We would like to say a special thanks to our contest judges for their support of this endeavor! We could not have done this without you!
| Contest Judges | |
|---|---|
|
Bill Bemister, AIT Technology Support Services Jay Bieszke, Facilities Terrance Campbell, Graduate Admissions Tony Dawson, Auxiliary Services Rob Falbo, WC Dell Technologies Representative Amanda Franklin, Risk Management/Legal Affairs Becki Henderson, Student Development Annie Huang, Marketing Communications |
Billy Keller, AIT Infrastructure and Security Craig Mulligan, AIT Operations Bob Norris, Public Safety Steve Oberg, Library and Archives Josh Okerman, Center for Vocation and Career John Welsh, HoneyRock Craig Williams, AIT Enterprise Applications Alan Wolff, Chief Information Officer |
Group Video Submission Winners
1st Place: Siobhan Sinnamon, Alexander Park, Sarah Park
2nd Place: Joanna Moss, Phoebe Jeske
3rd Place (one of two): Jordan Lee, Daniel Her, Nathan Hayslett
3rd Place (two of two): Christopher Kempen, Stephen Stoscher, Hannah Morris, Emma Wilson, Clayton Weaver, Katie O'Connor (submitted for WC Concert Choir)
Individual Video Submissions Winners
1st Place: Isaiah Cochran
2nd Place: Josh Sunderland
3rd Place: Nicholas Meriwether
Check out all video submissions on AIT's YouTube Channel!
There will be SIX awards given out for this contest. Submit with a group of friends, or on your own! 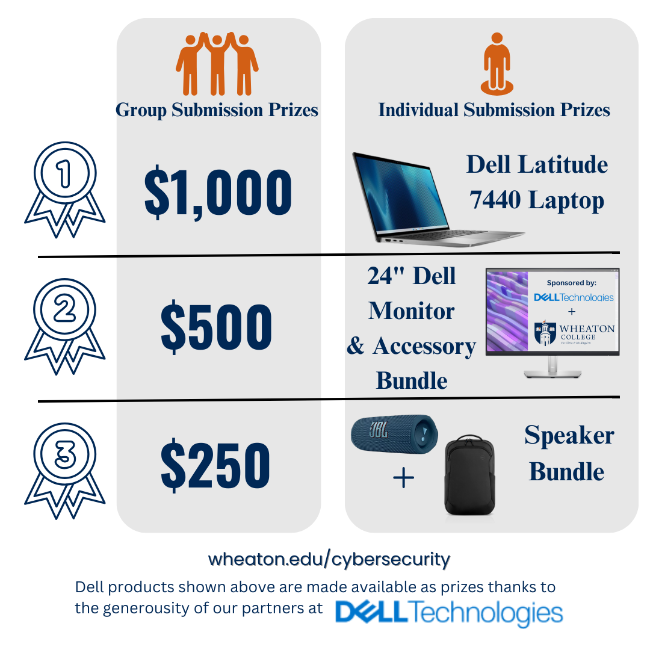 FAQ's:
FAQ's:
- Who is eligible to participate? This contest is open to all current graduate and undergraduate Wheaton College students.
- Can I submit more than one video? Yes! Be sure to complete a new jotform for each submission (see guidelines below for instructions on how to submit your videos). All submissions are due by 11:59p CST on Nov 13th DEADLINE EXTENDED to Dec 4th.
- How are winners selected? A judging committee will vote on videos submitted using the Contest Judging Rubric during the week of December 4th. AIT will announce the winners by 12p CST on December 8th.
- I won! How do I collect my prize? AIT will be contacting you using the information submitted on your entroy form to ensure you receive your prize.
- My friends and I submitted a video as a group. How does it work if we win? AIT will contact each person based on the information entered on the submission jotform. Prize money will be divided evenly among all members of the group.
- My student organization submitted a group video. If we win, can the prize money go to the student organization's budget? Yes, if you win a group submission and you designate an official Wheaton College Student Club or Organization on your group submission form, we can transfer the money to that budget.
QUESTIONS? Email us! academic.institutional.technology@wheaton.edu
Submit your video by completeing these two steps:
-
- Post video on Instagram; tagging @WheatonAIT
- Complete the appropriate form for your submission
- Video entries should be 30-90 seconds in length and must be original work
- Entries will be accepted through 11:59 PM CST December 4th, 2023
- A Wheaton College Wheaton College Media Release Form must be completed for each person distinctly featured or involved in the production of the video
- By submitting a video entry, the creators authorize use by Wheaton College as part of our cybersecurity awareness campus efforts
- All video content must be align with Wheaton College’s including mission, Statement of Faith and Community Covenant
- A committee will vote on winning videos during the week of Dec 4th using this Contest Judging Rubric
- AIT will announce the winners by 12p CST on Dec 8th
Video content must NOT:
- Promote illegal behavior
- Discriminate against or support individual prejudice towards others along ethnic, racial, religious, or sexual grounds
- Invade the privacy of any person
- Use inappropriate or obscene images or language
- Violate the Wheaton College Community Covenant
This contest is open to all current graduate and undergraduate Wheaton College students.
QUESTIONS? Email us! academic.institutional.technology@wheaton.edu
- Email security (best practices)
- Phishing(what is it? how to spot it)
- Social Engineering
- Password security/safety
- Password best practices
- What defines a good password
- Password managers
- Cyber apocalypse (what can happen, horror stories if we DON’T follow best practices)
- Ransomware (what can happen)
- Cover the personal, campus, and community risk/negative impact
- Career
- What it’s like to be a cybersecurity professional (general and/or within Wheaton College)
- Be the SHIELD (Cybersecurity as a career)
